HIPAA, short for the Health Insurance Portability and Accountability Act, comprises complex guidelines designed to safeguard the confidentiality of patients’ sensitive health information. You must ensure HIPAA compliance during the verification of patient benefits.
HIPAA compliance is applicable to any organization or individual that creates, receives, maintains, or transmits protected health information (PHI). Healthcare providers, insurance companies their business partners, like medical billing and health insurance eligibility verification companies, have access to PHI. Ensuring HIPAA compliance implies complying with regulations on the handling of PHI.


Your patients’ privacy is paramount!
Contact us today for reliable, secure, and compliant health insurance verification support.
PHI and Insurance Eligibility Verification
Health insurance verification, a key step in the medical billing process, involves confirming the patient’s insurance coverage, benefits, and eligibility. By managing each step efficiently, medical practices can ensure correct billing, prompt reimbursement, prevent claim rejection, and improve the patient’ s overall experience.
HIPAA is comprised of two vital regulations: Privacy and Security. The Privacy Rule covers the handling of patient data, preventing the improper use of sensitive information. The Security Rule focuses on protecting electronic health records from cyber threats. Both PHI and ePHI are protected under the Privacy Rule, though the Security Rule mostly relates to ePHI.
Insurance eligibility verification specialists are required to handle patient data healthcare at all stages of the process. PHI covers details about an individual’s physical or mental health condition, the corresponding treatment, or the associated payment. Additionally, it includes any information within the same record set that either identifies the subject of health, treatment, or payment data or could be utilized for identification purposes.
Examples of PHI include various medical records such as test results, x-rays, scans, physician’s notes, diagnoses, treatments, eligibility approvals, claims, and remittances. In addition to these, it extends to names, phone numbers, email addresses, Medicare Beneficiary Numbers, biometric identifiers, details about emotional support animals, and any other information that can lead to identification.
All forms of PHI records fall under the purview of HIPAA when held by a covered entity or a business associate, including entities like insurance verification companies. This coverage extends to diverse formats of PHI records, including spoken PHI, information on paper documents, electronic PHI, and both physical and digital images that have the potential to identify the subject of health information.
Ensuring HIPAA compliance requires ensuring that PHI is handled with the highest standards of security during the process. Safeguarding patient information during health insurance eligibility verification requires adherence to the Privacy Rule for both oral and written communications, along with compliance with the Security Rule for electronic transactions.

For insights into compliance and quality assurance in insurance verification,
explore our post about Compliance and Quality Assurance in Insurance Verification
Navigating HIPAA Compliance in Healthcare Insurance Verification
HIPAA compliance in insurance eligibility verification is integral to maintaining patient privacy and ensuring secure data exchange. Here are the key aspects of HIPAA regulations for insurance verification in medical practices:
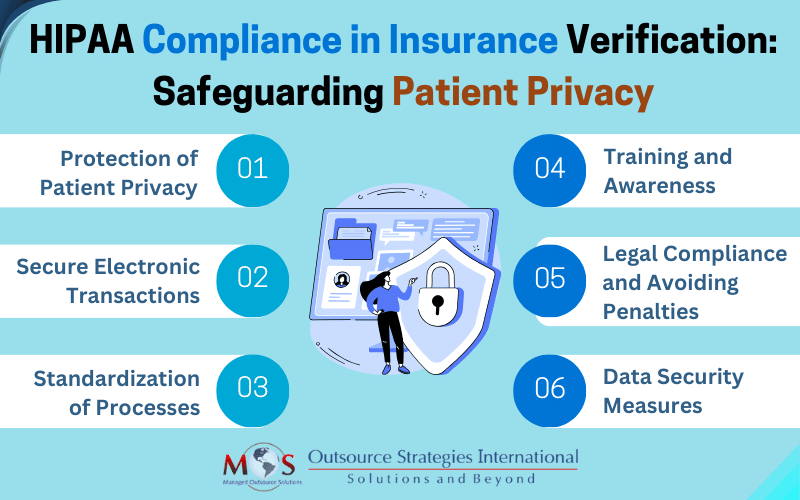
Protection of Patient Privacy
Insurance eligibility verification involves collecting patient demographic and insurance information, including their name, date of birth, insurance policy number, and group number. The patient’s identity is verified by checking the patient’s photo ID, insurance card, and other relevant documents. HIPAA requires secure handling of this information.
Secure Electronic Transactions
To verify patient coverage and benefits, the provider will contact the insurance company via telephone or a web portal. HIPAA mandates secure electronic data interchange standards to protect the integrity and privacy of the information exchanged during these transactions.
Standardization of Processes
HIPAA establishes standardized processes and code sets for various healthcare transactions, including those related to insurance eligibility verification. The transactions and code set standards apply to patient-identifiable, health-related information transmitted electronically. They are based on electronic data interchange (EDI) standards, which allow the electronic exchange of information from computer to computer without human involvement. Standardization enhances the consistency and efficiency of data exchange, reducing errors and ensuring a smoother verification process.
Training and awareness
HIPAA mandates training for healthcare staff regarding the proper handling of PHI and compliance with privacy and security rules. In the context of insurance eligibility verification, training ensures that staff members understand and follow the established protocols, reducing the risk of privacy breaches.
Legal compliance and avoiding penalties
Healthcare providers need to comply with HIPAA regulations to avoid legal repercussions and penalties. Compliance with HIPAA regulations helps providers navigate the process to meet legal requirements and avoid fines, sanctions, and damage to their reputation.
Data security measures
HIPAA requires safeguarding electronic PHI (ePHI) through encryption, access controls, and regular security assessments. HIPAA compliance ensures that adequate security measures are in place to protect electronic data from unauthorized access or breaches when at rest and during transmission.
Partner with a HIPAA-compliant Insurance Verification Company
HIPAA compliance in insurance eligibility verification is integral to maintaining patient privacy, ensuring secure data exchange, standardizing processes, and avoiding legal issues for non-compliance. If your medical practice outsources patient eligibility verification, make sure you partner with a fully HIPAA-compliant service provider. Such companies will have necessary safeguards and protocols in place to protect PHI. They will ensure that PHI is handled with the utmost care, reducing the risk of unauthorized access, breaches, or mishandling of sensitive information. This not only ensures compliance with legal requirements but also contributes to building trust with patients and maintaining the integrity of your medical practice.

Protect sensitive health information with our HIPAA-compliant insurance verification services!