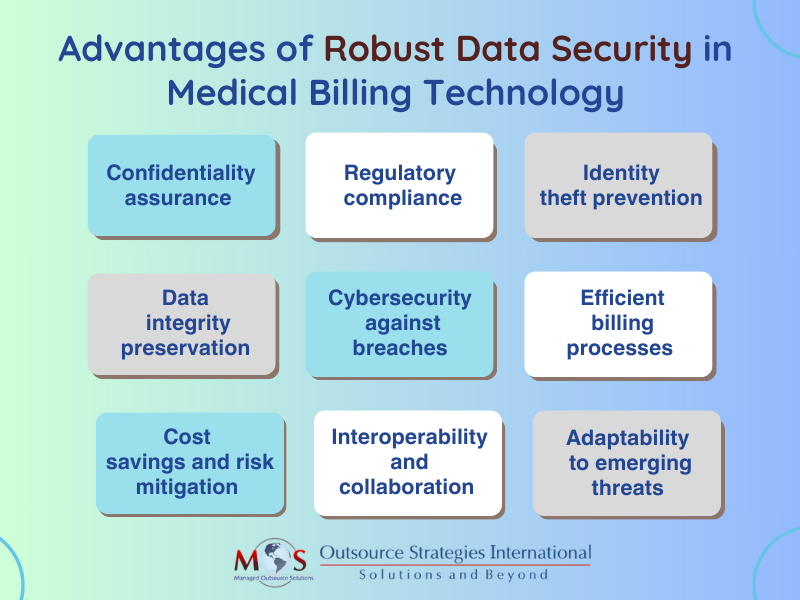
Medical billing systems handle a vast array of data, including patient details, treatment codes, and financial transactions, making them attractive targets for cyber threats. Therefore, securing healthcare billing data is crucial during medical billing processes. The role of technology in medical billing is key, as it facilitates the automation, efficiency, and accuracy of the entire process of medical billing services. Patient confidentiality, financial integrity, and regulatory compliance relies on the safeguarding of sensitive information throughout the billing process.
A breach in information protection impacts patient privacy and poses serious legal and financial consequences for healthcare providers. To build patient trust and maintain the integrity of the healthcare ecosystem, it is important to implement stringent information security measures. These include encryption protocols, access controls, regular audits, and compliance with industry regulations such as HIPAA. By prioritizing data protection in medical billing systems, healthcare entities not only protect themselves from potential breaches but also contribute to a safer and more resilient healthcare environment for patients and providers alike.

Challenges in Data Security Measures in Medical Billing
Major reasons for challenges in data security measures in the medical billing process include outdated technology, poor staff training, and lack of compliance with regulations. These challenges can have a severe impact on the revenue cycle, resulting in significant financial losses, legal penalties, and damage to the reputation of the provider.
Comprehensive information security measures also have a direct impact on reimbursement rates. Healthcare providers that invest in sufficient security measures typically enjoy higher reimbursement rates compared to those that do not. The stringent information protection expectations set by insurance companies and government programs are met by providers adhering to these standards, resulting in increased reimbursement rates as a reward.
Best Practices for Billing Data Protection
Here are key measures that can be implemented in healthcare coding and billing systems to safeguard sensitive information:
Encryption protocols:
Advanced encryption algorithms serve as a critical safeguard for sensitive patient and financial information. By implementing these protocols, healthcare billing systems ensure that sensitive data transmitted between various components of the healthcare ecosystem, including providers, insurers, and billing entities, remains confidential and secure. This also helps healthcare organizations comply with regulatory requirements such as HIPAA and fosters trust among patients and stakeholders, contributing to the overall integrity and reliability of the medical billing process.
Access controls:
Access controls define and manage permissions, ensuring that only authorized personnel can access specific information within the system. Restricting unauthorized access to sensitive billing data allows only authorized personnel to view or modify information. This enhances the overall security and facilitates compliance with healthcare regulations such as HIPAA. Access controls contribute to the confidentiality, integrity, and availability of RCM data, instilling confidence in patients and stakeholders regarding the secure management of sensitive healthcare information.
Authentication mechanisms:
Authentication mechanisms in these systems typically involve the use of multifactor authentication, requiring users to provide multiple forms of identification such as passwords, smart cards, or biometric data. By implementing strong authentication protocols, healthcare organizations reduce the risk of unauthorized access and data breaches.
Regular audits and monitoring:
Conducting regular audits and real-time monitoring of system activities to detect and respond to any suspicious or anomalous behavior ensures the integrity of the billing system. Practices can also ensure compliance with industry regulations such as HIPAA and detect and rectify any discrepancies in billing records promptly.
Firewalls and intrusion prevention systems:
It is ideal to deploy firewalls and intrusion prevention systems to monitor and filter network traffic, preventing unauthorized access and protecting against potential cyber threats. These technologies together can create a formidable barrier, safeguarding sensitive patient and financial data from cyberattacks. Continually analyzing and filtering network traffic, firewalls and IPS not only prevent unauthorized access but also contribute to the overall resilience of the billing infrastructure.
Employee training and awareness:
A well-informed and trained staff plays a key role in preventing security breaches and ensuring compliance with regulatory standards such as HIPAA. Providing ongoing training to employees on information protection best practices and fostering a culture of awareness helps minimize the risk of human error or unintentional breaches. Training programs educate employees about the latest cybersecurity threats, data protection protocols, and the proper handling of sensitive information.
By implementing these measures, technology-driven billing systems can enhance confidence in users, protect sensitive information, and contribute to a secure and trustworthy healthcare billing environment.